8 Signs It’s Time to Upgrade Your Access Control System (NYC Edition)
How to Recognize Security Gaps Before They Put Your NYC Property at Risk
In New York City, the speed of business is relentless. You cannot afford for your operations to grind to a halt because a door won't open, or worse, because a door opened for the wrong person.
We often ask business owners a simple question: How important is your security infrastructure to your daily success? If operations are disrupted by technical glitches, does your business lose money? Do you have assets or proprietary information that require strict protection?
If you answered yes, then treating your security system as an afterthought is a liability you cannot afford.
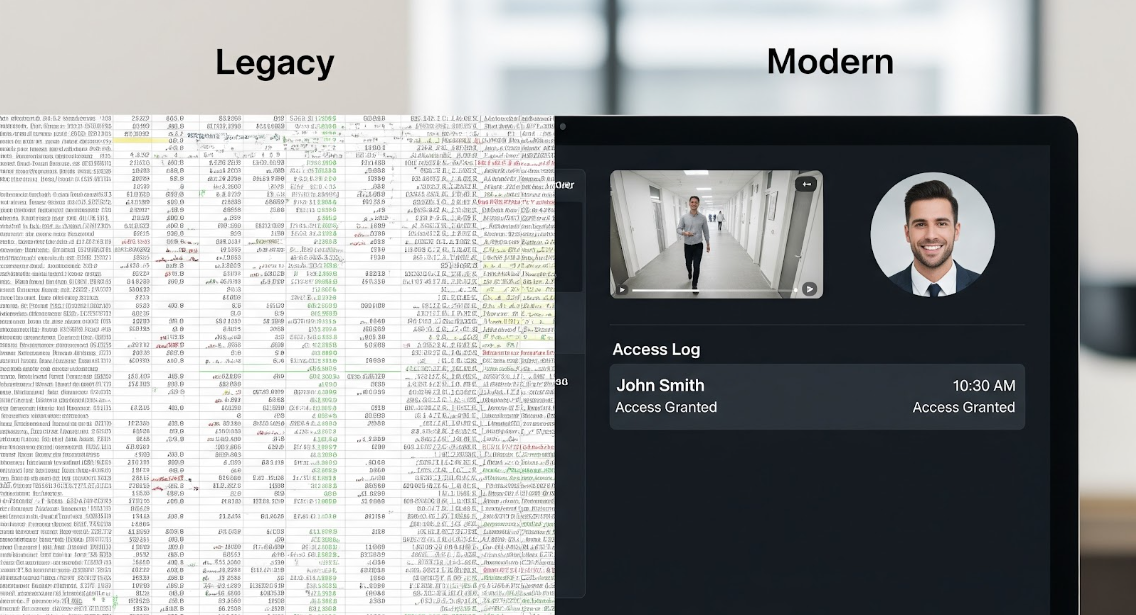
Many businesses in the NYC metropolitan area rely on "legacy" systems. These are the beige boxes and clunky readers installed fifteen or twenty years ago. They might still technically function, but they are increasingly vulnerable to security breaches, difficult to manage, and expensive to maintain.
As a dedicated ICT contractor and integrator, Streamline Telecom has seen the good, the bad, and the ugly of NYC security infrastructure. We believe in being the most reliable and fair partner for our clients. We do not disappear after the contract is signed, and we take pride in delivering work that is clean, organized, and effective.
If you are unsure whether your current setup is up to the task, here is a practical guide to the eight clearest signs that it is time to retire your legacy hardware and upgrade to a modern access control solution.

1. Your Hardware Is Showing Physical Wear and Inconsistency
The most obvious sign of a failing system is physical degradation. Access control isn't just software; it relies heavily on electric lock hardware to physically secure the door. This includes electromagnetic locks, electric strikes, and exit devices.
In a high-traffic NYC office, a single door might cycle thousands of times a month. Over time, the internal solenoids in electric strikes wear out, or the alignment on maglocks shifts due to door frame settling.
The "Jiggle" Test
If your employees know that they have to pull the handle, jiggle it, and then scan their card for the door to unlock, your system is failing. Security shouldn't require a "magic touch."
Furthermore, take a look at your readers. Are they cracked? Sun-bleached? unresponsive to key fobs unless held at a specific angle? This isn't just a nuisance; it slows down foot traffic and frustrates staff. When hardware becomes temperamental, employees often resort to propping doors open, which defeats the entire purpose of your Access Control Systems.
2. You Are running "Zombie" Servers
Many older access control systems are "on-premise," meaning they run on a dedicated computer server located somewhere in your building's IT closet. This server is the brains of the operation. It records activity and distributes data to the control panels.
The problem arises when the computer running this software is outdated. We frequently encounter access control servers running on Windows 7 or even Windows XP. Microsoft has long since stopped supporting these operating systems, meaning they no longer receive security patches.
If your access control server is connected to your network, it is a cyber-security vulnerability. Hackers can exploit unpatched operating systems to gain entry to your broader data network.
The Crash Risk
Beyond security, there is the risk of hardware failure. Old hard drives spin until they don't. If your server crashes and you do not have a robust backup, you could lose your entire user database, forcing you to manually re-enter every employee and re-issue every card. Modern solutions, like the cloud-based systems we install from Avigilon Alta vs Unity Access Control NYC, eliminate this risk by hosting the "brains" securely in the cloud.
3. Credential Management Is a Bottleneck
Who holds the keys to your building? In many legacy systems, adding or removing a user is a tedious process that requires a specific person to be physically present at the server terminal.
If your office manager is on vacation and a new employee needs access, or an employee is terminated and needs access revoked immediately, you are stuck.
The "Key Guy" Problem
If your security relies on one person knowing how to navigate a complex, antiquated software interface, your business is vulnerable.
Modern systems allow for remote management. With platforms like Avigilon Alta, administrators can adjust credentials, schedules, and permissions from any device, anywhere in the world. You can grant a vendor temporary access to a service elevator for two hours on a Saturday without leaving your house. If your current system doesn't offer this flexibility, it is costing you time and administrative overhead.
4. Your Cards Are Easily Cloned (The Low-Frequency Risk)
Take a look at the proximity card in your wallet. If it is a standard "125 kHz" proximity card (often bulky and white), it is relying on technology that dates back to World War II.
These older cards broadcast a facility code via a simple resonant circuit. They are incredibly easy to clone. Anyone can buy a cloning device online for less than $30, stand near you in a coffee shop or elevator, and copy your card's signal in seconds.
The Encryption Gap
If you want true security, you need to upgrade to smart cards (like MIFARE DESFire) or Mobile Credentials NYC. These use advanced encryption and mutual authentication between the card and the reader. They prevent the "clone wars" scenario where unauthorized duplicates are floating around your city.
Upgrading your Access Control Installation to support encrypted smart cards or mobile credentials is one of the most effective ways to instantly harden your physical security.
5. Lack of Integration with Video Security
In the past, security systems operated in silos. You had a burglar alarm, a camera system, and an access control system, and none of them spoke to one another.
Imagine an alarm goes off at the back door at 2:00 AM. Your access control log says "John Doe" entered. But was it really John? Or did John lose his card? Without video integration, you have data, but you don't have verification.
The Unified View
Modern security is unified. We specialize in Avigilon Unity and Alta systems where video and access control are merged. When a specific event occurs – like a forced door or an access denied alarm – the system instantly tags the relevant video footage.
This allows security teams to verify events in real-time. You can view access activity alongside live footage on a single dashboard. If your current system forces you to look at a timestamp on a door log and then manually search through hours of video footage on a separate DVR to see who it was, your system is obsolete.
6. Your Employees Hate the User Experience
User experience matters in security. If a system is annoying to use, people will find ways to bypass it.
We live in a world where we pay for coffee with our watches and unlock our cars with our phones. Requiring employees to carry a separate plastic fob or card feels archaic.
The Mobile Shift
Mobile access control is the new standard. Systems like Avigilon Alta utilize Bluetooth and NFC to allow "touchless" entry. An employee can leave their phone in their pocket or bag, wave their hand near the reader, and the door unlocks.
This is not just cool tech; it is practical. It eliminates the cost of buying replacement plastic cards. It solves the "I forgot my badge" problem. If your current system cannot support mobile credentials, you are missing out on a massive gain in workplace efficiency and morale.
7. You Have No Audit Trail or Compliance Reporting
For many NYC businesses—especially in finance, legal, healthcare, and logistics—knowing who went where is a matter of legal compliance.
If you have a server room, a records room, or a pharmaceutical storage area, you need a rock-solid audit trail. Legacy systems often have limited memory or clunky reporting tools that export confusing text files.
Data-Driven Security
Modern cloud-based systems provide granular reporting. You can run reports on specific doors, specific users, or specific times of day instantly. You can spot anomalies, like an employee trying to access the warehouse at midnight on a Sunday.
Avigilon’s intelligent algorithms can even detect abnormal behavior and alert operators in real-time. If your current system cannot tell you who is in your building right now, it is time to upgrade.
8. You Cannot Find Support (The "Ghost" Vendor)
This is perhaps the most critical sign. You need a replacement reader or a new control board, but your original installer has gone out of business, or the manufacturer has discontinued the product line.
We see this often. A business is stuck with a proprietary system that no reputable integrator wants to touch because parts are unavailable. You are essentially holding onto a ticking time bomb.
The Streamline Difference
At Streamline Telecom, we pride ourselves on reliability. We are dedicated to our timelines and fast, responsive communication. We don't go missing. When we install a system, we set a world-class level of expectation on the cleanliness and organization of the wiring and infrastructure.
We believe that the infrastructure we install should look like it belongs on the cover of a magazine. It should be labeled, organized, and accessible. If your current system is a "bird's nest" of tangled wires installed by a ghost vendor, it is a liability. You need a partner who stands behind their work.
Consider reviewing your broader security setup as well. Often, an access control upgrade is the perfect time to evaluate your Commercial Security Cameras to ensure full compatibility.
The Hidden Cost of Waiting
Security directors and business owners often hesitate to upgrade because of the perceived disruption. They worry about drilling noise, dust, and downtime.
We understand this concern. However, working with a professional ICT contractor changes the dynamic. When Streamline Telecom manages a project, we aim to beat our own timelines. We work to minimize disruption to your day-to-day operations.
We recently helped Age Group LTD, a global apparel company on Park Avenue, who needed a rapid turnaround. They had been ghosted by another contractor. We provided a quote within 24 hours, identified faulty cabling from previous vendors, and delivered a fully functional system (plus AV installation) in just four days.
That is the difference between a "cable guy" and a professional integrator.
Future-Proofing with Cloud and AI
The future of access control is not just about locking doors; it is about business intelligence.
By moving to cloud-based systems like Avigilon Alta, you get instant software updates. You never have to pay a technician to come on-site just to update firmware. Your system actually gets smarter over time as new features are released.
You also gain the ability to scale. Whether you are securing a single office in Manhattan or a multi-site enterprise across the boroughs, cloud systems grow with you without requiring expensive server hardware upgrades.
"Security convergence is no longer a buzzword; it’s a requirement. The ability to verify access control events with video verification is the baseline for modern facility protection." — Security Industry Association (SIA)
Next Steps for Your Business
If your system is showing these signs of age, do not wait for a critical failure to act. A locked-out building or a security breach costs far more than a planned upgrade.
We can assess your current infrastructure, identify the weak points, and propose a solution that fits your specific needs—whether that is a simple retrofit of your readers or a full migration to a cloud-based environment.
Would you like Streamline Telecom to perform a site inspection and provide a fair, transparent assessment of your current access control risks?
Contact us today to ensure your business remains secure, accessible, and professional.